Posts by Emory Vandiver
The Huge ROI of Achieving NIST 800-171 Compliance for CMMC
Why the ROI Can Be Significant When You Achieve NIST 800-171 Compliance for CMMC The National Institute of Standards and Technology (NIST) is the agency that promotes the highest cybersecurity standards for public and private sector IT networks. This agency has updated Special Publication 800-171 to help protect sensitive government data that may be found…
Read MoreReal-World Examples of Cybersecurity Nightmares That Could Have Been Avoided – Part 3
Security and compliance awareness training transforms a company’s greatest security risk — its people — into its greatest defensive asset. When companies empower their employees through security awareness training, they gain a host of unbeatable benefits like reduced security costs, increased compliance, and a big edge against cyberattacks. Over our 3 Part Series, each scenario…
Read MoreReal-World Examples of Cybersecurity Nightmares That Could Have Been Avoided – Part 2
Security and compliance awareness training transforms a company’s greatest security risk — its people — into its greatest defensive asset. When companies empower their employees through security awareness training, they gain a host of unbeatable benefits like reduced security costs, increased compliance, and a big edge against cyberattacks. Over our 3 Part Series, each scenario…
Read MoreReal-World Examples of Cybersecurity Nightmares That Could Have Been Avoided – Part 1
Security and compliance awareness training transforms a company’s greatest security risk — its people — into its greatest defensive asset. When companies empower their employees through security awareness training, they gain a host of unbeatable benefits like reduced security costs, increased compliance, and a big edge against cyberattacks. Over our 3 Part Series, each scenario…
Read MoreCMMC 2.0: 5 Key Changes
For better or worse, CMMC is now CMMC 2.0 – this is the result of the Pentagon’s recent CMMC internal review process. It will affect different DoD Contractors in different ways, bringing minor to moderate changes, depending on their individual CMMC compliance aspirations or requirements. CMMC 2.0 — What’s New? The Department of Defense…
Read MoreEnsure Cyber Risk Management Doesn’t Impede Business Performance
Cyber security has become a priority for most organizations, and rightly so. Data breaches are a real risk, and cybercriminals aren’t going away. The “prohibition” approach (or “zero trust”), which limits access to web pages and applications, is a go-to model for data protection. But are security programs interfering with business performance? Research suggests that…
Read MoreCyber Security – A Top Business Risk….and Opportunity in 2021
Cyber security remains a critical element to any organization as cyber threats continue to become increasingly sophisticated, expensive, and disruptive. As detailed below, there are many high-profile examples of cyber breaches, however it’s very important to understand that the same risk level applies to every company equally – regardless of size, industry etc. According to…
Read MoreWarning – IT Service Providers should NOT be Assessing Themselves or Their Customers
A lot of businesses today rely upon cloud-based systems to operate. These include the use of cloud-based storage, online marketing systems, digital media, social media marketing, and so on. But as reports of data breaches and security threats continue to increase, clients and customers need some extra reassurance that the company they are doing business…
Read MoreKnow About the DFARS Interim Rule 11/30/20 Deadline re: CMMC Compliance?
SUMMARY: DoD is issuing an interim rule to amend the Defense Federal Acquisition Regulation Supplement (DFARS) to implement a DoD Assessment Methodology and Cybersecurity Maturity Model Certification (CMMC) framework in order to assess contractor implementation of cybersecurity requirements and enhance the protection of unclassified information within the DoD supply chain. DATES: Effective November 30, 2020.…
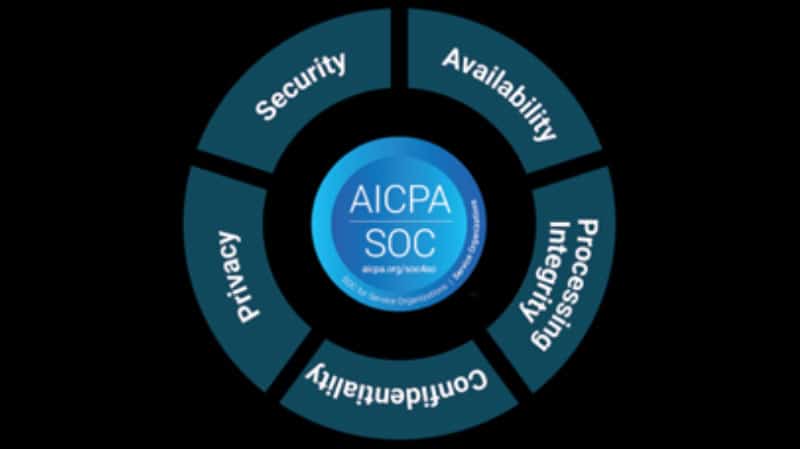
Read MoreUnderstanding SOC 2 and Deciding Which Principles Are Right Your Company
If you’re a service company such as a cloud or SaaS provider, you need to pass what’s called the System Organization Controls (SOC) 2 audit. Passing the audit shows that you take cybersecurity seriously. But how do you pass? Well, you need to: Choose which of the 5 SOC 2 principles apply Instruct an assessment based on…
Read More