CMMC – Cybersecurity Maturity Model Certification
CMMC Overview
Simply put, the Department of Defense (DoD) Contractor community is now required to build and maintain a proper cybersecurity posture to help protect the US from its adversaries. The official CMMC rollout will occur over several years to encompass all contracts and suppliers.
The original CMMC (Cybersecurity Maturity Model Certification) framework was released January 31, 2020. However, the most recent version, CMMC 2.0, was unveiled in November 2021.
Who Needs CMMC certification?
All DoD contractors will be required to comply with CMMC, at some level, in order to bid on DoD contracts.
What is CMMC 2.0?
For better or worse, CMMC is now CMMC 2.0 – this is the result of the Pentagon’s recent CMMC internal review process. It will affect different DoD Contractors in different ways, bringing minor to moderate changes, depending on their individual CMMC compliance aspirations or requirements.
CMMC 2.0 — What’s New?
Nonetheless, a main criticism since the beginning has been that smaller DoD Contractors won’t be able to afford the changes required to comply with CMMC (i.e., IT spend, consulting fees and assessment cost). Hence several of the changes within CMMC 2.0 are geared to address is this issue.
The Biggest Changes to CMMC:
1. Transition Levels have been Eliminated
CMMC 1.0 contained five maturity levels. This new version removes the transition levels—Level 2 and Level 4—creating a cleaner model with just three CMMC levels.
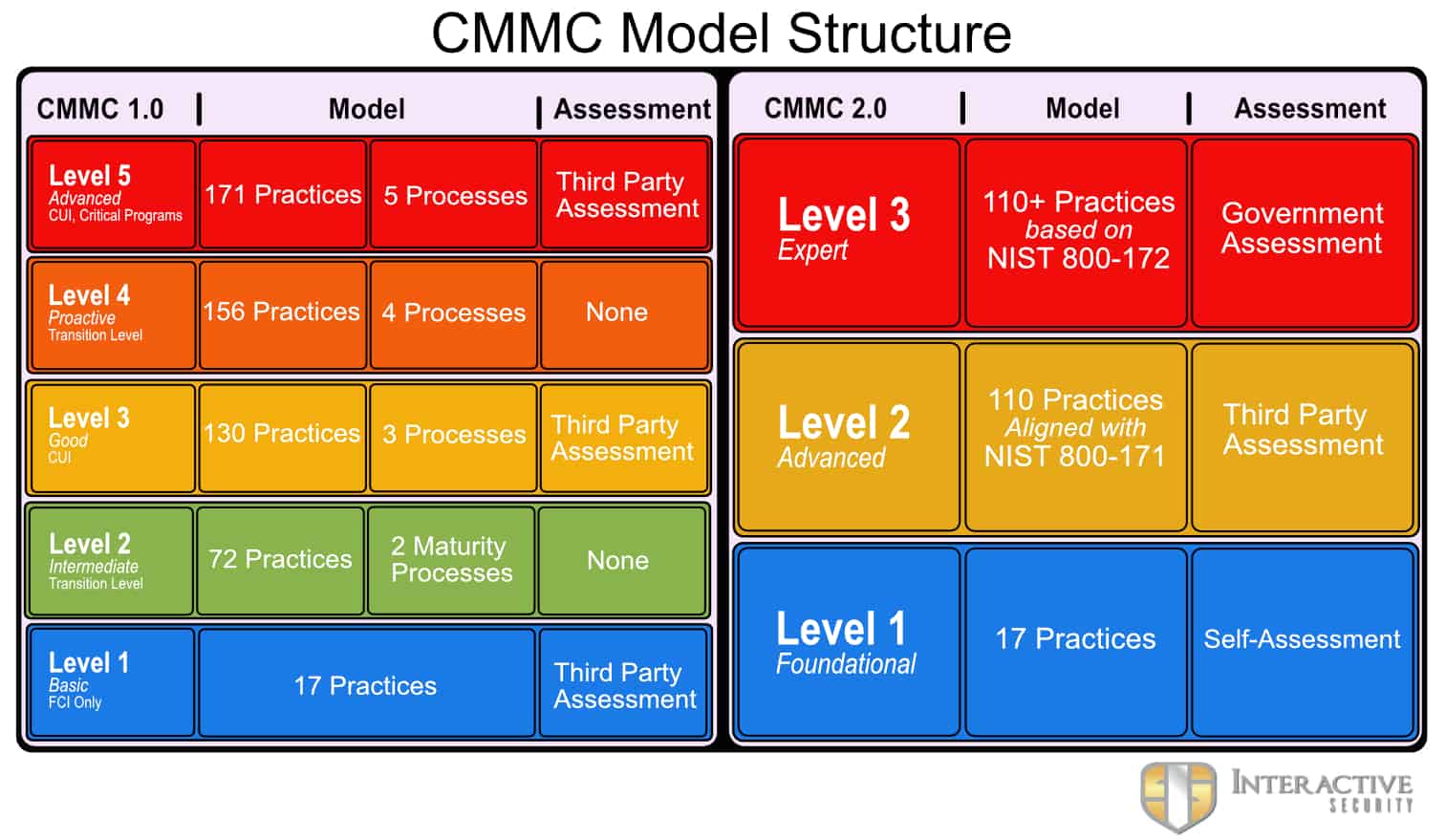
CMMC 2.0 Level 1 (Foundational)
Remains the required level for companies who don’t handle Controlled Unclassified Information (CUI) but only handle Federal Contract Information (FCI).
CMMC 2.0 Level 2 (Advanced)
Replaces the original CMMC Level 3. This is the required level for Contractors who handle CUI. However, it only contains 110 of the 130 practices in the original Level 3. This aligns with the NIST 800-171 compliance requirements.
CMMC 2.0 Level 3 (Expert)
Now contains the more stringent requirements of the original Level 5. Very few Contractors will require this specialized level of cybersecurity.
2. Third-Party Assessments are not Required for Level 1
This is VERY controversial and many people believe this change ultimately will not stand. The primary reason CMMC was born was to validate that Contractors were handling data properly. CMMC 2.0 eliminates the third-party assessment validation requirement in favor of a self-assessment. Critics of self-assessments point to their historically poor outcomes - compliance is actually never achieved.
3. Twenty Additional Practices Eliminated
Contractors handling CUI will need to achieve CMMC 2.0 Level 2 or Level 3. However, the 20 additional practices (above the original 110 controls of NIST SP 800-171) required under the original CMMC, have been eliminated.
4. Maturity Processes Eliminated
CMMC 2.0 no longer contains the maturity processes of the original version. This helps reduce the required documentation and removes some vagueness from the old model.
5. Plan of Action and Milestones (POAMs) are Permitted
The previous version of CMMC was a pass/fail model. In order to pass an assessment, there could be no deficiencies. CMMC 2.0, similar to past DFARS requirements, Contractors are permitted to submit a time-bound “Plan of Action and Milestones” to cover certain areas of non-compliance.
POAM’s provide a way to achieve compliance without having a perfect assessment. They document a formal time-framed reasonable plan to remediate any outstanding gaps in compliance. The DoD will determine the POAM’s remediation timeframe so that a re-assessment can be performed in order to validate the POAM items have been remediated.
One important caveat – certain practices are not permitted for a POAM because they are deemed too critical. Such items will still require full compliance.
The Effect on DoD Contractors
If there’s anything we know to be certain, its uncertainty and change are unavoidable when it comes to cybersecurity, especially when it involves Government.
Any organization preparing for CMMC, should be proud they made the decision to do so. They are likely ahead of their competition and ultimately, they will have a significant competitive advantage – CMMC (at whatever version) is not
going away. Although it is not yet officially in Defense contracts, it will be and, in the meantime, Contractors must continue to meet the self-assessment requirements of the DFARS Interim Rule - (NIST 800-171).
The biggest mistake a contractor can make is to stop preparing for CMMC because it’s on the way, and every contractor will still require some level of certification, self-assessed or otherwise.
We’re Here to Help
Interactive Security has been on the front lines of CMMC & NIST 800-171 compliance for many years. We’re here to help by continuing to navigate these uncertain waters and provide understanding on the latest CMMC changes. Our staff of CMMC-AB Registered Practitioners (RPs) are officially recognized to provide CMMC consulting, specifically trained to help prepare for and achieve CMMC compliance.
Our clients receive customized one-on-one consulting from our expert team. We help DoD Contractors satisfy NIST/CMMC requirements by:
Understanding the requirements with their specific environment
Training their leadership, staff, IT professionals and relevant third parties
Assisting with the DFARS Interim Rule’s basic self-assessment and submission to SPRS.
- Initial Gap Analysis
- Remediation Guidance & Coordination
- Policy / Procedure Writing
- Formal Documentation Writing (SSP & POAM)
Acting as liaison throughout CMMC third-party certification assessment
Providing ongoing compliance maintenance items
- Internal Risk Assessment
- SSP & POAM Maintenance
- Vulnerability Scanning
- Penetration Testing
- Security Awareness Training
- Email Phishing Training
CMMC does not need to be an overwhelming challenge - Interactive Security can make it seamless.
