Our Clients are Our Partners - we believe in transparency, clarity and trust. Since 2007, this approach has allowed us to achieve the ultimate goal - transition Cybersecurity Compliance away from fear and uncertainty to a place of comfort and assurance.
At Interactive Security, our team of expert security specialists are former Chief Information Security Officers (CISO), and actually do the work - we’re not willing to insert novice “rinse and repeat box checkers” where seasoned experts are needed.
Our team is comprised of industry certified security professionals with uniquely qualified backgrounds spanning both third-party consulting and executive leadership roles within enterprise companies. Technology is complex and security requirements are fluid; and we know it’s critical to closely understand our clients in full view - in technology and business terms.
Interactive Security is proud to offer a variety of core solutions to meet our client's cybersecurity and compliance needs regardless of industry and company size. We make Cybersecurity Compliance ~ Obtainable, Simple and Affordable.


.png)
Expert guidance for CMMC 2.0 and NIST 800-171, helping DoD contractors stay compliant, secure, and contract-ready.

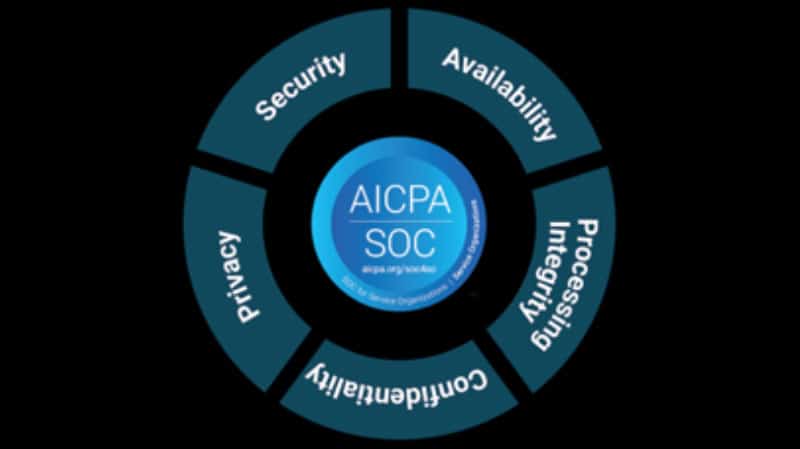
Independent SOC 1 and SOC 2 assessments that verify internal controls and strengthen trust with customers and auditors.

HIPAA security and privacy assessments that identify risks, validate safeguards, and help ensure full regulatory compliance.

Real-world attack simulations that uncover security weaknesses and deliver clear reporting with actionable remediation steps.

.avif)
.avif)
.avif)
.avif)
.avif)
.png)

















For over a decade, Interactive Security has been a premier provider and innovator in Cybersecurity and Compliance for organizations across the globe.




























.jpg)




























.jpg)