CMMC Philadelphia PA
CMMC Overview
The Cybersecurity Maturity Model Certification (CMMC) is a unified standard for implementing cybersecurity across the defense industrial base (DIB), which includes over 300,000 companies in the supply chain. Released January 31, 2020, CMMC is the new requirement for U.S. DoD contractors, replacing the self-attestation model and moving towards third party certification.
The U.S. DOD is migrating to the new CMMC framework in order to assess and enhance the cybersecurity posture of the U.S. Defense Industrial Base (DIB). The CMMC is intended to serve as a verification mechanism to ensure appropriate levels of cybersecurity controls and processes are adequate and in place to protect controlled unclassified information (CUI) that resides on contractor / subcontractor networks.
The certification is built on existing requirements such as NIST SP 800-171 (mainly), NIST SP 800-53, AIA NAS9933, private sector contributions, and input from academia. The CMMC will consist of 5 levels to measure the cybersecurity practices of contractors.
Who Must Comply With The CMMC?
While the CMMC was initially built for DoD contractors who will eventually be required to obtain a CMMC certification, its widely accepted that CMMC will soon become the replacement requirement for any organization wanting to do business with any federal, state, and local government entities. This includes all suppliers at all tiers along the supply chain, small businesses, commercial item contractors and foreign suppliers.
CMMC will act as a procurement gate that a contractor must pass to even be eligible to bid on, win or participate on a contract - without a valid CMMC certification (Level 1 through 5), the prime and/or sub will be barred from the contract. It is conservatively estimated that between 200,000 - 300,000 organizations will be in scope for CMMC, with many of those not being considered traditional defense contractors. The reason for that is the trickle-down effect of third parties that have the ability to impact the confidentiality and/or integrity of Controlled Unclassified Information (CUI) where it is stored, transmitted, and/or processed.
Contractors remain responsible for implementing critical cybersecurity requirements, but the CMMC changes this paradigm by requiring third-party assessments of contractors' compliance with certain mandatory practices, procedures and capabilities that can adapt to new and evolving cyber threats from adversaries.
The Cybersecurity Maturity Model Certification Framework
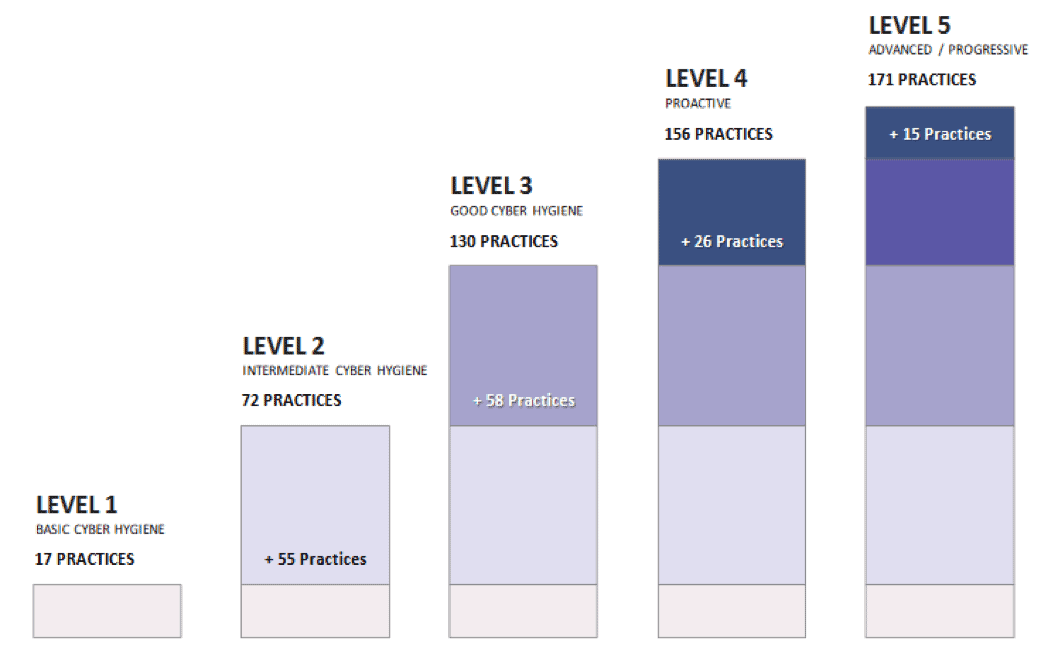
The CMMC establishes five certification levels that reflect the maturity and reliability of a company's cybersecurity infrastructure to safeguard sensitive government information on contractors' information systems. The five levels are tiered and build upon each other's technical requirements. Each level requires compliance with the lower-level requirements and institutionalization of additional processes to implement specific cybersecurity-based practices.
Overview of the relevant processes and practices of each level:
Level 1: A company must perform "basic cyber hygiene" practices, such as using antivirus software or ensuring employees change passwords regularly to protect Federal Contract Information (FCI). FCI is "information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government." It does not include public information or certain transactional information.
Level 2: A company must document certain "intermediate cyber hygiene" practices to begin to protect any Controlled Unclassified Information (CUI) through implementation of some of the US Department of Commerce National Institute of Standards and Technology's (NIST’s) Special Publication 800-171 Revision 2 (NIST 800-171 r2) security requirements. CUI is "any information that law, regulation, or government-wide policy requires to have safeguarding or disseminating controls," but does not include certain classified information.
Level 3: A company must have an institutionalized management plan to implement "good cyber hygiene" practices to safeguard CUI, including all the NIST 800-171 r2 security requirements as well as additional standards.
Level 4: A company must have implemented processes for reviewing and measuring the effectiveness of practices as well as established additional enhanced practices detect and respond to changing tactics, techniques and procedures of advanced persistent threats (APTs). An APT is defined as an adversary that possesses sophisticated levels of expertise and significant resources that allow it to create opportunities to achieve its objectives by using multiple attack vectors.
Level 5: A company must have standardized and optimized processes in place across the organization and additional enhanced practices that provide more sophisticated capabilities to detect and respond to APTs.