SOC 1 AUDITS
SOC 1 examinations, also known as SSAE 18 reports, are designed for organizations that provide services that impact their customers’ financial statements or internal controls over financial reporting. SOC 1 reports are commonly requested by customers who are public or operate in highly regulated industries. Examples of organizations who receive SOC 1 reports include:
The control objectives for a SOC 1 report are defined by the service organization based on the objectives relevant to their customers. Control objectives include a combination of IT controls and relevant business process controls.
SOC 2 AUDITS
System and Organization Control 2 examinations are more technical in nature and focus on one or more trust service principles – security, availability, processing integrity, confidentiality, and privacy. All SOC 2 examinations include a set of core common criteria that are addressed by the security principle. The criteria for availability, processing integrity, confidentiality, and privacy are separate and can be added based on the specific software or services provided by the service provider. SOC 2 reports are relevant to service organizations that are relied upon for the operational needs of their customers or for protecting sensitive customer data. Software as a Service providers and companies in industries such as FinTech, HealthTech, EdTech, Data Science, Artificial Intelligence, and Security can benefit from a SOC 2 report. The control objectives for a SOC 2 report are defined by the American Institute of Public Accountants (AICPA) and are primarily supported by IT controls.
System and Organization Control for CYBERSECURITY
SOC for Cybersecurity examinations are appropriate for any organization with cybersecurity risks, including businesses and not-for-profits. SOC for Cybersecurity is an entity-wide assessment of your organization’s cybersecurity risk management program. Reports can be used by organizations to communicate the effectiveness of their cybersecurity risk management program, building trust and confidence in their market.
Types of Reports:
Type 1
Report just provides a report of procedures / controls an organization has put in place as of a point in time.
Type 2
Report has an audit period and provides evidence of how an organization operated its controls over a period of time.
It is important to understand that there are not more stringent control requirements in a Type 2 SOC Report; but rather, it describes how a company’s control environment operated over its audit period (typically not less than six months). You can have the same controls in a Type 1 report as the Type 2; the only difference is that they are audited or examined over a period of time and testing results are reported in a SOC 1 and SOC 2 report.
Value and Benefits of Being SOC Compliant
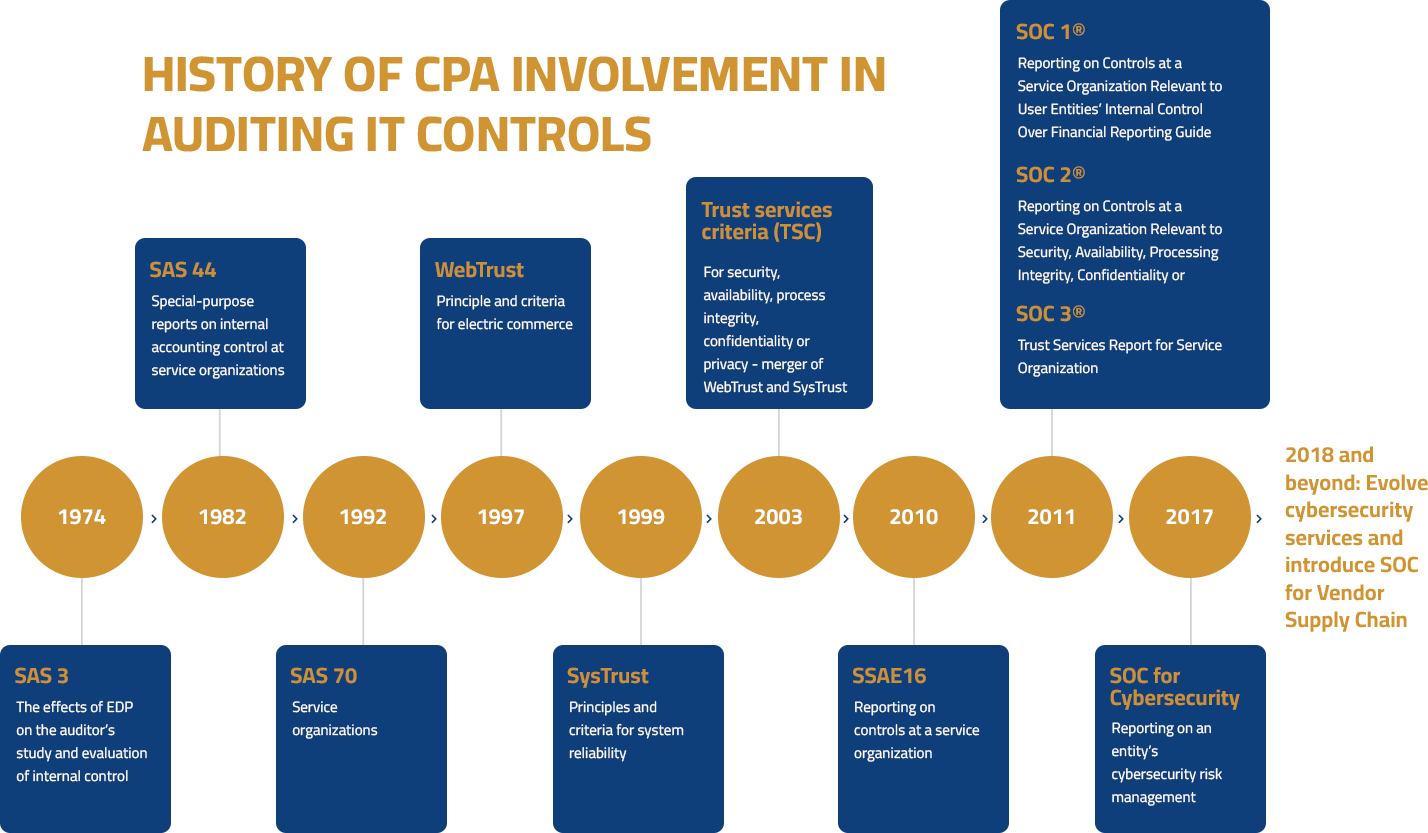
1970s
CPAs required to consider effects of electronic data processing on the evaluation of internal control in financial statement audits.
1990s
CPAs begin performing SAS 70 audits to report on the effectiveness of internal control over financial reporting.
2000s
CPAs begin using the trust services criteria for evaluating controls relevant to security, availability, processing integrity, confidentiality and privacy and issuing SOC reports to address vendor management needs related to outsourced services.
2017
Introduction of SOC for Cybersecurity attestation services for CPAs to report on the effectiveness of controls within an organization’s cybersecurity risk management program.
2018 and beyond
Continue to evolve cybersecurity services and introduce SOC for Vendor Supply Chain to enable users of products produced, manufactured and distributed by an entity to better understand and manage risks, including cybersecurity risks, arising from their business relationships with the entity.
(Source: Whitworth, Martin. “The 13 Global Providers That Matter Most and How They Stack Up.” The Forrester Wave”: Information Security Consulting Services, Q1 2016. Jan. 29, 2016
