Now is the Time to Get Ready for CMMC
On January 31, 2020, the US Department of Defense (DoD) rolled out the long-awaited Cybersecurity Maturity Model Certification (CMMC). So if you’re a DoD contractor,…
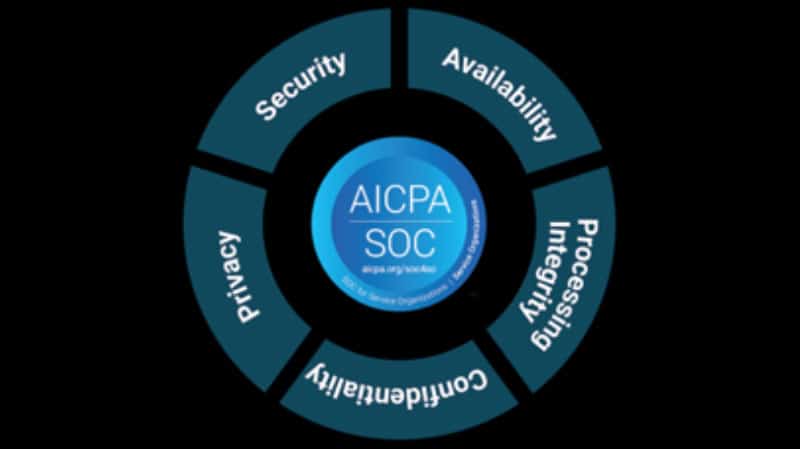
Understanding SOC 2 and Deciding Which Principles Are Right Your Company
If you’re a service company such as a cloud or SaaS provider, you need to pass what’s called the System Organization Controls (SOC) 2 audit. Passing…
Remote Workers – Implementing a Risk Based Cyber Security Plan
The COVID-19 era has succeeded in making remote work mainstream, mainly because of quarantine and social distancing policies. While some companies and employees have…
Email Phishing – Your Organization’s Biggest Cyber Threat
All it takes is a single email for hackers to gain access and steal company data. Whenever an email lands in your inbox, there’s…
CMMC – Cyber Security Requirement for all DoD Contractors
The DoD’s Cybersecurity Maturity Model Certification (CMMC) is now in force, but what does this mean for DoD contractors? Well, every company must now prove…
Beware – Cyber Security Language in Your Third-Party Contracts
Cyber security is a constantly changing field with constantly changing requirements. Recently, companies have found increasing technical jargon inserted into their contracts with third…
Benefits of Using a Third-Party Cyber Security Service
Cybercriminals and terrorists never rest, not even during global pandemics. The cost will almost always weigh heavier on smaller businesses and organizations that lack…
Application Security Begins at Planning
Why Application Security Should Begin at Planning As cybersecurity threats become more potent and prevalent, the need to make apps more secure by identifying…
Managing Security Threats from Within
4 Tips for Managing Cybersecurity Threats from Within Most companies usually develop and implement cybersecurity strategies aimed at external threats. However, according to the…