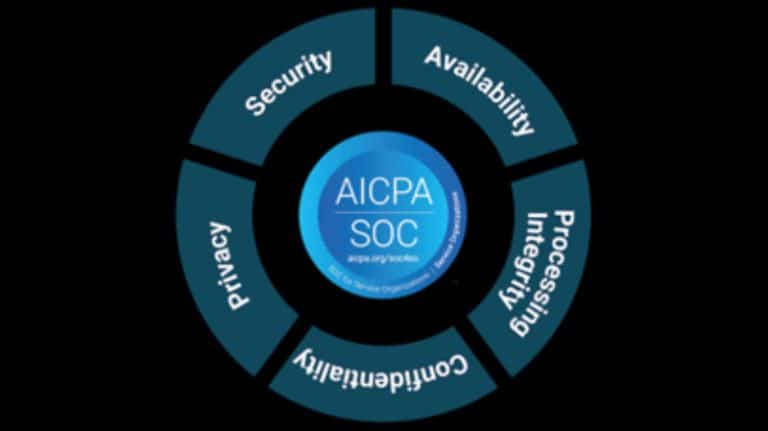
The Huge ROI of Achieving NIST 800-171 Compliance for CMMC
Why the ROI Can Be Significant When You Achieve NIST 800-171 Compliance for CMMC The National Institute of Standards and Technology (NIST) is the agency that promotes the highest cybersecurity standards for public and private sector IT networks. This agency has updated Special Publication 800-171 to help protect sensitive government data that may be found…